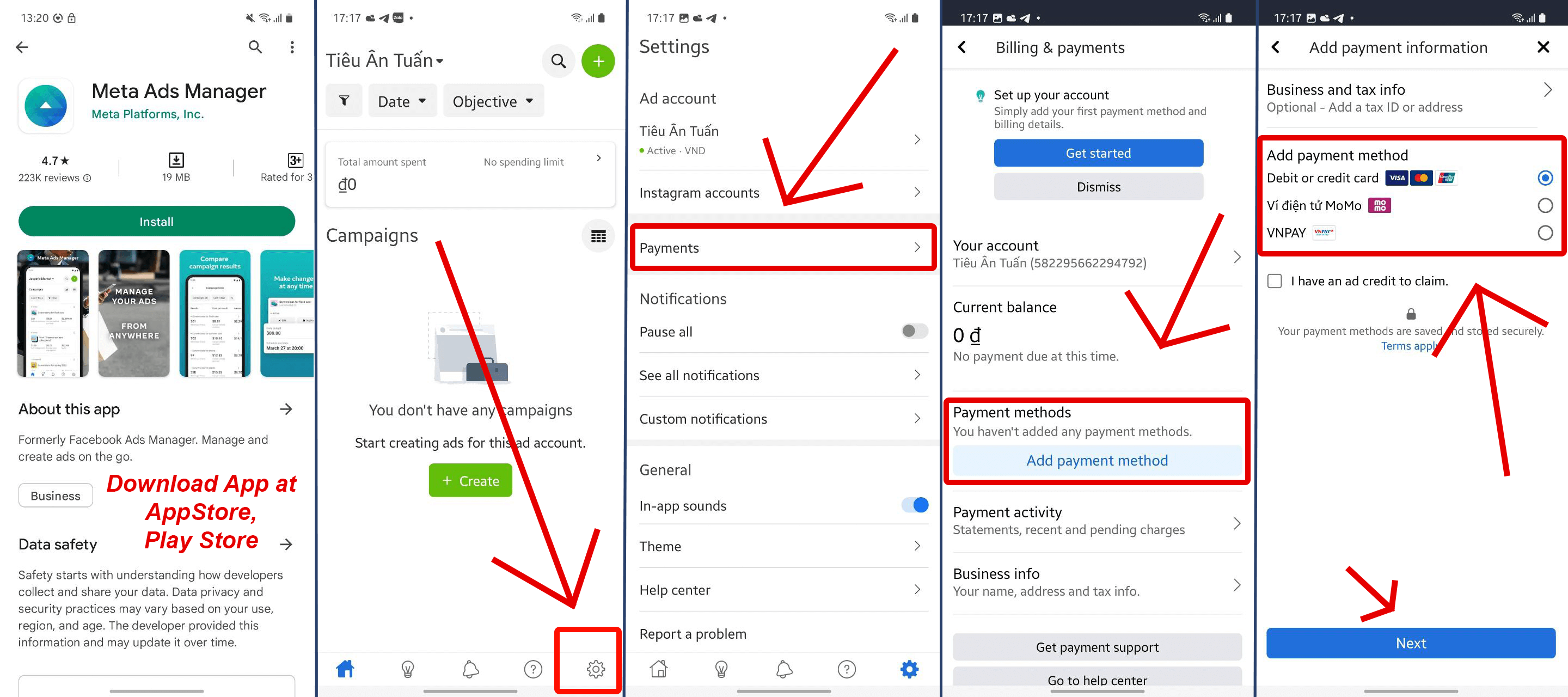
Security Protocols for Integrated Messaging: Safeguarding Communications on WhatsApp and Facebook
195 vỉew
Writing date: 2024-05-04 14:51:46

In the era of digital communications, ensuring the security of integrated messaging systems such as WhatsApp and Facebook is paramount, especially for sensitive business communications. Accnice writes this article reviewing the security measures and protocols in place to protect data and maintain privacy when using these platforms together.
Understanding Integrated Messaging Security
Understanding the security implications and the technology behind integrated messaging systems like those potentially between WhatsApp and Facebook is critical for maintaining user trust and safeguarding personal information. Here's a deeper look into the importance of secure communication and the current state of security features on both platforms:

1, Importance of Secure Communication
- Privacy Protection: Secure messaging ensures that only the intended recipient can read the message content, protecting against eavesdropping and unauthorized interception.
- Trust in Digital Platforms: Robust security measures are fundamental to building and maintaining trust among users, who are increasingly aware of digital privacy issues.
- Compliance with Regulations: Effective security practices help platforms comply with stringent data protection laws such as GDPR, which require the protection of personal data and privacy.
2, Current Security Features
WhatsApp Security
- End-to-End Encryption (E2EE): All personal and group chats on WhatsApp are protected with E2EE by default. This means that the content of messages is locked and cannot be accessed by anyone other than the sender and the recipients—not even WhatsApp or Facebook.
- Secure Data Storage: WhatsApp claims not to store messages on its servers once they are delivered, minimizing the risk of data breaches.
Facebook Security
- Transport Layer Security: Facebook encrypts communications between users and its servers using TLS, which protects the data in transit but does not prevent Facebook itself from accessing the content of messages.
- Optional End-to-End Encryption: Facebook offers E2EE as an opt-in feature through the "Secret Conversations" option in Messenger. This security feature aligns with WhatsApp’s encryption but is not enabled by default.
3, Challenges and Considerations
- Integration Complexity: Integrating WhatsApp’s E2EE into Facebook’s broader messaging ecosystem could pose significant technical challenges. Ensuring that the encryption protocols work seamlessly across different systems without compromising security is critical.
- User Education: As features evolve, educating users on how to utilize these security features effectively becomes increasingly important. Users need to understand the benefits of encryption and how to activate options like Facebook’s Secret Conversations.
- Balancing Security with Usability: There is often a trade-off between high security and ease of use. For instance, features like E2EE can complicate the user experience or limit certain functionalities, such as accessing messages across multiple devices.
- Legal and Privacy Considerations: Integrating systems must address varying global privacy standards and regulatory requirements, which can complicate the development and deployment of uniform security measures.
4, Future Outlook
As messaging platforms evolve and integrate, maintaining a high standard of security will be essential. Future developments might include:
- Advanced Encryption Technologies: As cryptographic methods evolve, newer forms of encryption might offer enhanced security without compromising usability.
- Unified Security Protocols: Developing a standardized security protocol across all messaging products within the Facebook ecosystem could help streamline security and improve user trust.
- Transparency Reports: Publishing detailed security and privacy practices, along with regular transparency reports, can help build user confidence and demonstrate a commitment to user data protection.
Overall, as Facebook and WhatsApp continue to integrate their messaging services, the focus must remain on robust security practices that protect user data while ensuring a seamless and user-friendly communication experience.
Enhancing Security in Integrated Messaging
Enhancing security in integrated messaging systems like those between WhatsApp and Facebook is essential to protect user data and maintain trust. Here’s how improvements can be made to ensure robust security in these integrated platforms:

1, Encryption Across Platforms
-
Unified End-to-End Encryption: By extending WhatsApp's end-to-end encryption to Facebook, all messages, regardless of their origin, would be encrypted from the sender's device until they reach the recipient's device. This would ensure that no intermediate servers or third parties, including the platforms themselves, could read the contents.
-
Consistent Security Standards: Apply the same rigorous encryption standards across all types of communications within the Facebook ecosystem, including instant messages, voice and video calls, and even stored data like shared media and back-ups.
2, Multi-Factor Authentication (MFA)
-
Comprehensive Implementation: Enforce MFA across all access points to the integrated messaging system. This includes not only app access but also account modifications, settings changes, and new device registrations.
-
Diverse Authentication Methods: Offer various MFA methods, such as text message verification codes, email links, biometric checks (fingerprint or facial recognition), or authenticator apps, giving users the flexibility to choose the most convenient and secure option.
3, Additional Security Measures
a, Advanced Security Protocols
-
Regular Security Audits: Conduct frequent and thorough security audits to identify and address vulnerabilities. These audits should cover both the software and hardware aspects of the platforms.
-
Real-time Threat Detection: Implement systems that monitor for unusual activities suggestive of breaches or attacks, such as unexpected large-scale data access, irregular login attempts, or the spread of malware.
b, Privacy Controls
-
User-Controlled Privacy Settings: Allow users to control who can message them directly and how their data is used for advertising or other purposes. This includes settings to manage the visibility of online statuses, read receipts, and profile information.
-
Transparent Data Policies: Provide clear, accessible information about what data is collected, how it is used, and who it is shared with. Regular updates to privacy policies and terms of service should be communicated clearly and directly to users.
c, Education and Awareness
-
User Education Programs: Create comprehensive education programs that help users understand the security and privacy features available. These should include guidance on enabling encryption, setting up MFA, and recognizing phishing attempts.
-
Community Engagement: Foster a community-oriented approach where users can report vulnerabilities, share security tips, and update each other on emerging threats. This could be supported through forums, webinars, and newsletters.
Enhancing security in integrated messaging involves a multifaceted approach that combines technology, user control, and education. By implementing these strategies, platforms like Facebook and WhatsApp can provide secure and private communication channels that protect against cyber threats and uphold user trust. Moving forward, continual adaptation and improvement of security measures will be essential as technology evolves and new threats emerge. This proactive approach in security and privacy will help ensure that integrated messaging not only enhances communication convenience but also maintains the highest standards of user safety.
Challenges in Integrated Messaging Security
Navigating the challenges of integrated messaging security, especially between major platforms like WhatsApp and Facebook, involves addressing several key concerns. Here’s an in-depth look at these challenges and potential strategies to manage them effectively:

1, Data Sharing and Privacy Concerns
a, Potential Data Leaks
- Vulnerability Assessments: Conduct regular vulnerability assessments to identify and mitigate risks associated with data sharing between the platforms.
- Encryption Enhancements: Strengthen encryption protocols to ensure that data remains secure when transferred between systems, especially where the security measures of one platform are not as robust.
b, Privacy Policy Alignment
- Unified Privacy Framework: Develop a unified privacy framework that addresses data handling practices across both platforms, ensuring that user data is managed in a consistent manner.
- Transparent Communication: Regularly communicate any changes in data usage or privacy policies to users in a clear and understandable way, ensuring that they are always informed about how their data is being used.
2, Regulatory Compliance
a, Adhering to Global Standards
- Compliance Teams: Employ specialized compliance teams to continuously monitor and adapt to new regulations across different regions, ensuring that all integrated messaging services remain compliant.
- Data Protection Officers: Appoint Data Protection Officers (DPOs) to oversee data management practices, ensuring they meet stringent legal standards like the GDPR.
b, Impact of Compliance on Operations
- Regulatory Mapping: Map out all applicable regulatory requirements and assess how they impact each element of the integrated messaging system.
- Proactive Adaptation: Stay proactive in adapting to changes in the regulatory landscape to avoid disruptions to service and potential legal challenges.
3, Technical and Implementation Challenges
a, Integration Complexity
- Advanced Integration Technology: Use state-of-the-art technology solutions to seamlessly integrate different messaging systems without compromising on security or functionality.
- Continuous Testing: Implement continuous integration/continuous deployment (CI/CD) practices for ongoing testing and refinement of the integration process.
b, Cross-Platform Compatibility
- Standardized Protocols: Develop standardized protocols for data exchange and communication between platforms, ensuring compatibility and reducing the chances of data loss or corruption.
- User Experience Focus: Maintain a strong focus on user experience, ensuring that integration enhances rather than complicates the usability of each platform.
Integrated messaging systems like those between WhatsApp and Facebook present complex security and privacy challenges that need careful management. By focusing on robust encryption, regulatory compliance, and clear communication policies, businesses can mitigate risks and safeguard user data. Additionally, embracing advanced technology and maintaining a proactive stance towards privacy and regulatory changes will be crucial for successful integration. These efforts will not only enhance security but also build trust with users, who are increasingly concerned about their digital privacy.
Implementing Best Practices for Secure Integrated Messaging
Implementing best practices for secure integrated messaging is essential for businesses to protect sensitive information and maintain trust with their clients and partners. Here are detailed strategies and best practices that businesses can adopt to ensure the security and integrity of their communication via platforms like WhatsApp and Facebook:

1, Regular Security Audits
-
Continuous Evaluation: Regularly schedule security audits to assess the vulnerabilities and risks associated with the integrated messaging systems. These audits should include penetration testing and the scanning of systems for any potential security loopholes.
-
Third-Party Assessments: Occasionally bring in independent security experts to evaluate the security measures. External reviews can offer a fresh perspective and uncover hidden vulnerabilities that internal teams might overlook.
2, Employee Training and Awareness
-
Regular Training Programs: Conduct ongoing training sessions to keep employees updated on the latest security practices and potential phishing scams or other cyber threats. Make this training a mandatory part of the onboarding process for new hires.
-
Simulated Attacks: Run simulated phishing attacks and other security drills to help employees recognize and react properly to suspicious activities. This proactive approach helps reinforce training and improve security awareness.
3, Use of Secure Business Tools
-
Enterprise-Grade Solutions: When possible, opt for enterprise versions of messaging apps like WhatsApp Business API, which are designed with additional security features to meet the needs of businesses, such as better data control and integration capabilities.
-
Custom Security Features: Leverage tools that offer customizable security settings, such as the ability to set expiration times for messages, control data storage, and manage device-level security policies.
4, Additional Best Practices
-
Data Encryption: Ensure that all data, both in transit and at rest, is encrypted. For integrations between different platforms, use protocols that support end-to-end encryption to prevent data exposure during transmission.
-
Multi-Factor Authentication (MFA): Implement MFA for accessing any part of the integrated system. This adds an additional layer of security, protecting against unauthorized access even if password details are compromised.
-
Privacy and Compliance: Stay informed about and compliant with international privacy laws such as GDPR, HIPAA (for healthcare-related communications), and others pertinent to your industry. Ensure that all integrations comply with these regulations to avoid legal penalties and protect user data.
-
Regular Policy Updates: Keep security policies and procedures updated to reflect new cybersecurity threats and technological changes. Encourage a culture of security within the organization by making these policies accessible and understandable for all employees.
Conclusion
By adhering to these best practices and continuously evaluating their effectiveness, businesses can significantly enhance the security of their integrated messaging systems. This proactive approach not only protects sensitive information but also builds trust with customers and stakeholders, crucial for long-term success in an increasingly digital world. As technology evolves, so too should the strategies we employ to protect it, ensuring that communication remains both efficient and secure.
For more insights and updates on effective social media strategies, make sure to follow Accnice and our tutorial blog, where we share the latest and most effective content marketing tips.